|
Keys and secrets in code repositories have led to major data breaches and significant financial loss. An AWS secret key accidentally pushed to GitHub on a Friday reportedly led to a loss of $64,000 by Monday morning, as 244 virtual machines were spun up. The attacker who stole 57 million user and driver records from Uber appears to have made use of an AWS credential within a private GitHub repository with permissions to the S3 bucket used as a database backup. Why do developers put keys and secrets in code repositories? Developers and DevOps engineers want to automate application and infrastructure deployment and the most straightforward way to do this can be to include the necessary keys and secrets in code. Sometimes this starts off as an initial proof of concept, but then ends up in production. It's also easy to accidentally push a credential to a repository. I've done this myself with an Azure service principal credential. Fortunately it was a repository on a private network with limited access. How can I discover keys and secrets in code repositories?
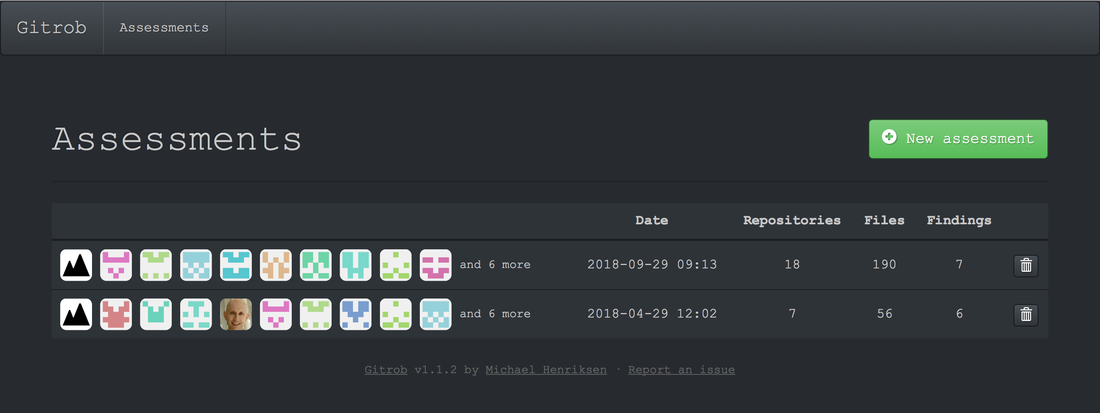
I've created a Github repository and deliberately included some keys and secrets. As it's a small repository, you can probably find them all manually. You can also scan using a tool such as GitRob. Click on the Read More link to find out more.
0 Comments
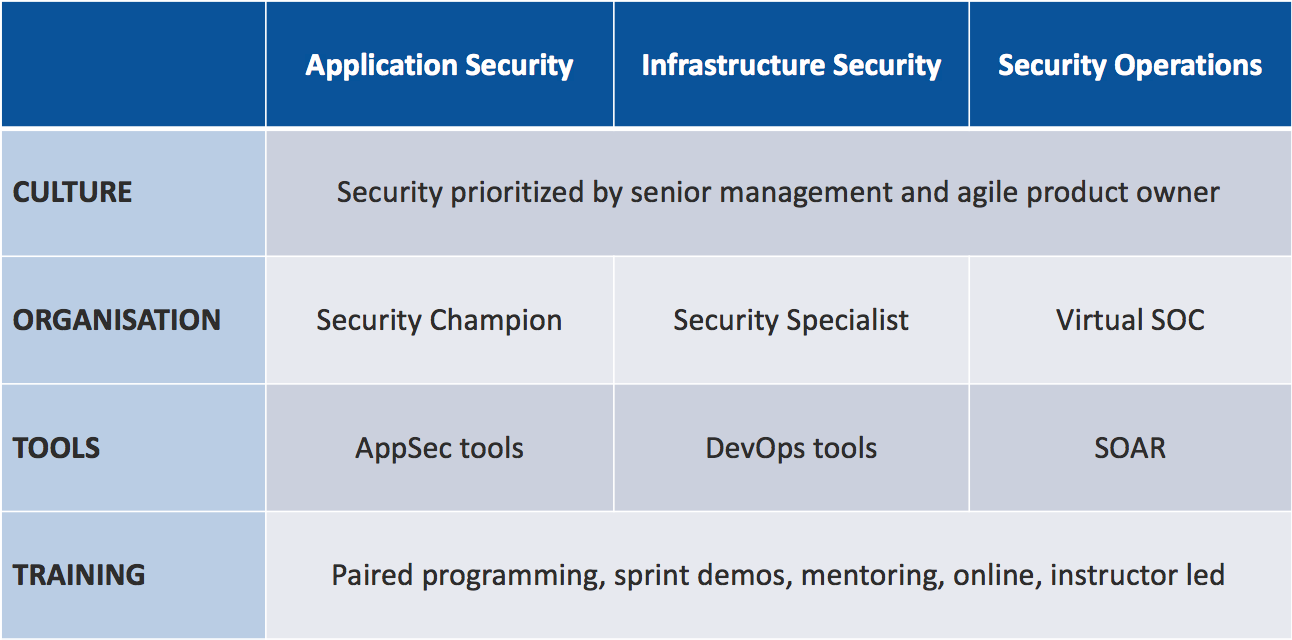
DevSecOps is a new way of working as described in my blog "What is DevSecOps? And Why is it needed?" As I was developing the training course DevSecOps Hands-on I realised I needed a DevSecOps framework encompassing the elements making up DevSecOps, which I then used to define the topic areas of the course at a high level: The DevSecOps Framework shows the various aspects which together encompass effective DevSecOps within an organisation, spanning application security, infrastructure security and security operations.
to see more on culture, organisation, tools and training as applied to DevSecOps, click on the "Read More" link .......  Over the last few years there have been a large number of data breaches from S3 buckets, for example:
Some of the data breaches were simply due to the S3 bucket being configured as public instead of private. AWS improved the S3 console recently, to clearly warn the user when a bucket or object is being made public. But I know some DevOps engineers who only ever use code and never log in to the console - so they would never see these warnings. The Dow Jones case I find interesting because the misconfiguration arose from the use of "authenticated users" in the access control list. You might think that means an authenticated user of the same AWS account the S3 bucket resides in. Actually it means any AWS account in the world. The Uber S3 bucket wasn't misconfigured as such - it appears that an attacker got hold of GitHub credentials, so could access private Git repositories, the attacker then discovered an AWS key which had rights to the S3 bucket. Effectively protecting an organisation against cloud security incidents such as these requires an in-depth understanding of cloud security architecture, security expertise relating to cloud provider services, combined with a DevSecOps approach to infrastructure code development, testing and deployment. DevSecOps has been described as "security as code", "a marriage of DevOps and Security" and "shifting security to the left".
Traditional security approaches are inefficient and largely ineffective for organisations using Agile, DevOps and Cloud - as illustrated by the massive amount of recent data breaches. DevSecOps is a new approach which embeds security to each DevOps team, with automated security testing at all stages of the software development lifecycle. Security infrastructure, policies, controls, compliance, audit and even secure operations are all coded and automated, with almost no manual processes. This is the basis of a new course I've developed, DevSecOps Hands-on which I'll be delivering at QA's International House in London early October. |
AuthorPaul Schwarzenberger is a Cloud Security Architect and DevSecOps specialist Archives
July 2024
Categories |
|
Celidor Limited
Company Number: 08870661 |


 RSS Feed
RSS Feed