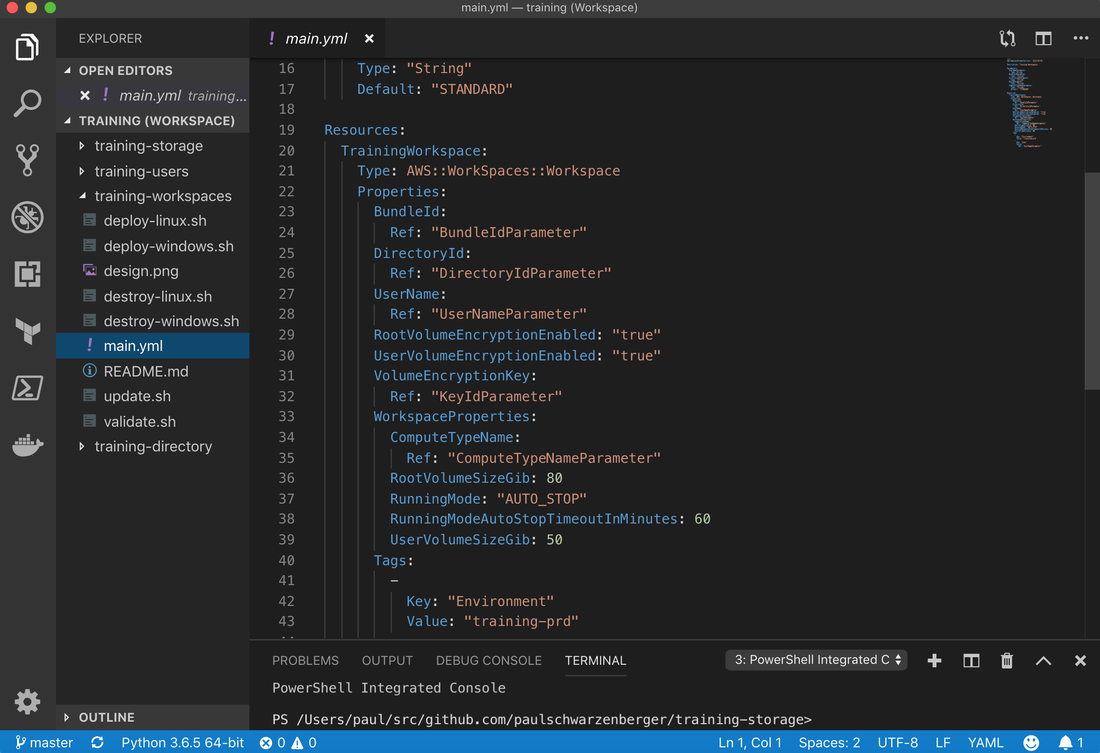
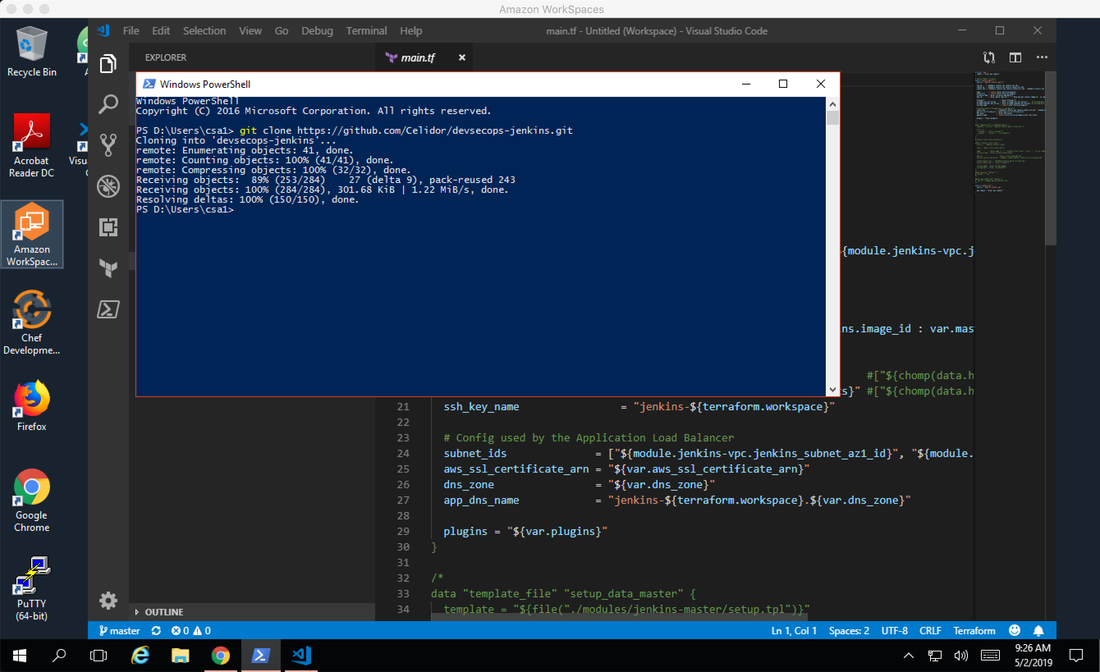
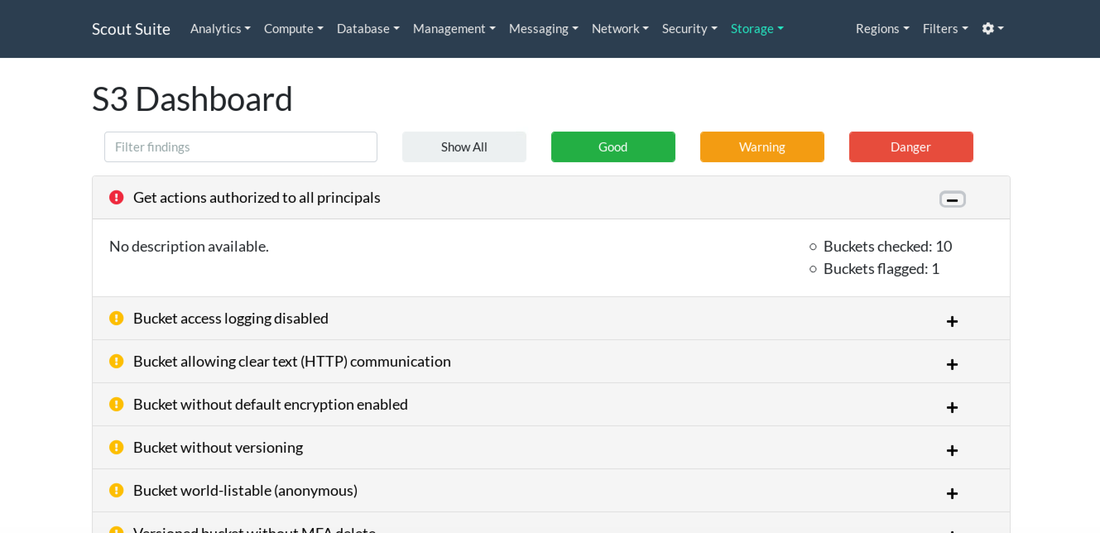
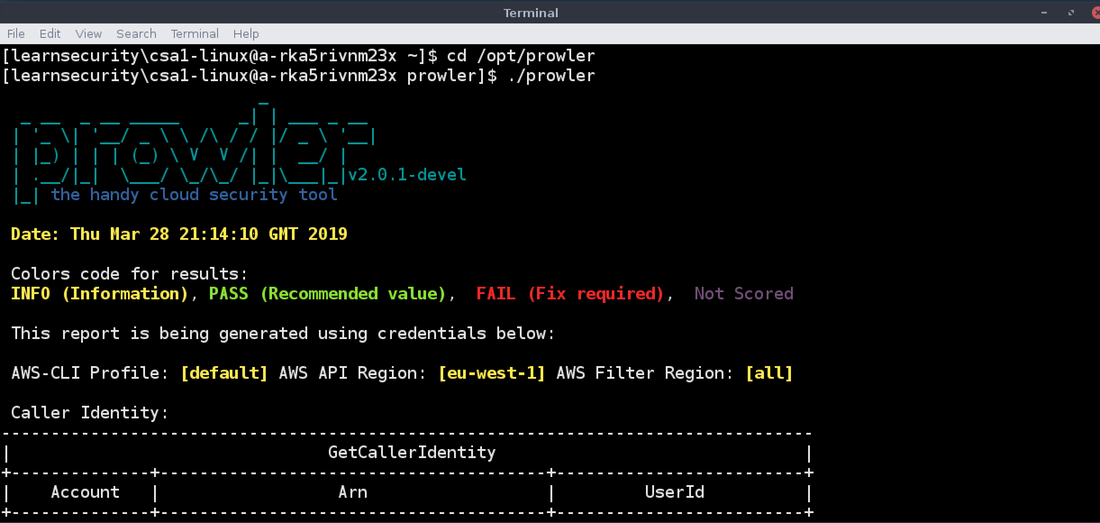
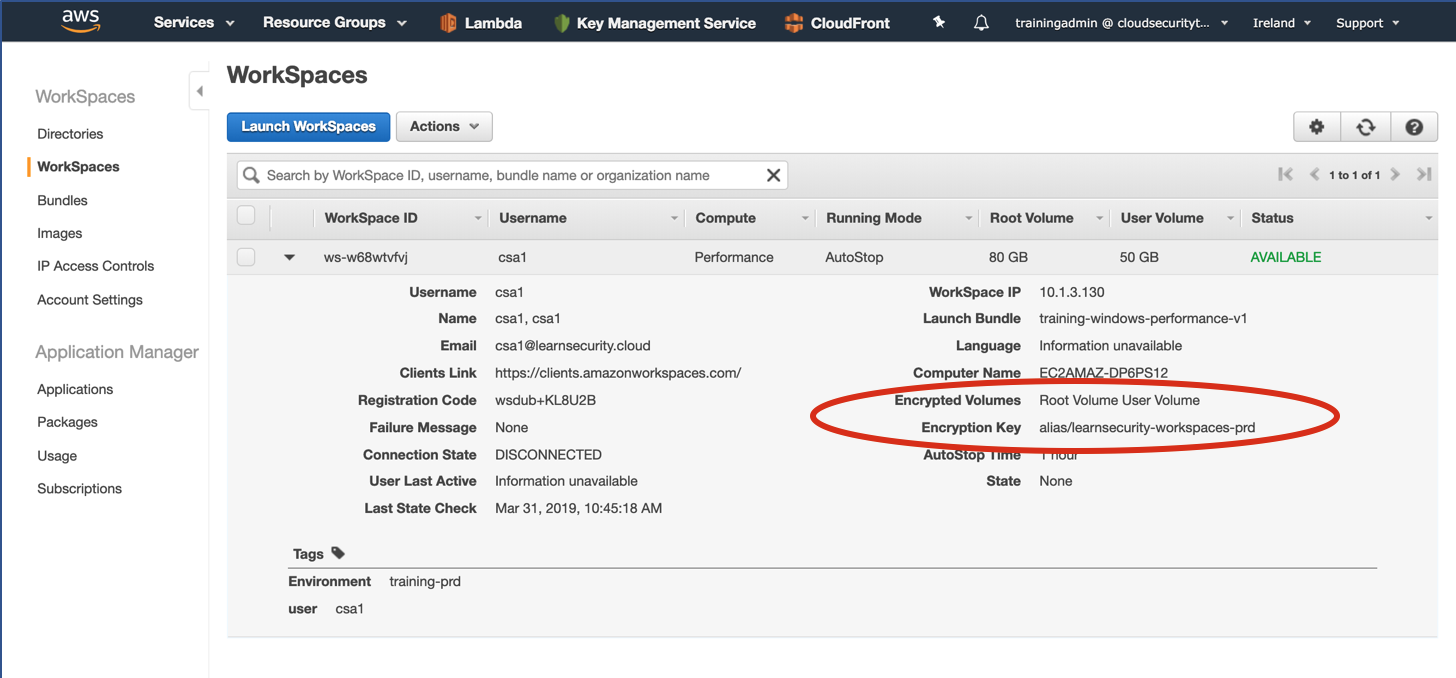
Part 4: security featuresMy 44CON Cloud Security and DevSecOps training course this June includes AWS, Azure and GitHub accounts which the students use so they don’t need to create their own. As I described in Part 1, I also decided to build a training platform, so that students can connect to a virtual desktop in the cloud with all the software they need pre-installed. That way they can come on to the course with any laptop or even tablet which supports the Amazon WorkSpaces client. I built the supporting infrastructure in AWS using Terraform which you can read about in Part 2 of my blog, and then scripted user setup across all environments as described in Part 3. Click on the "Read More" link below to see the security features I built in to the system. So finally I was ready to actually build virtual desktops using Amazon WorkSpaces in the real environment. As this isn’t currently supported by Terraform, I created an AWS CloudFormation template with parameters so it can be used for both Windows and Linux, specifying details such as the directory, image, boot and user volumes, number of processors and memory, and deployed from my laptop using a bash script. After a bit of tweaking to the script so I could loop through users 1 – 20, the WorkSpaces were deployed and I could test using the Amazon WorkSpaces client. The performance and usability was really good, and I spent some time installing the software tools needed for the labs and creating images. I ran through the course labs starting with the Windows virtual desktop. I tried out the applications and tools used in the labs – for example Git, Terraform, Visual Studio Code, AWS CLI and Azure PowerShell – and made sure they all worked as expected. Then I moved on to test the Linux image for the compliance lab, where we use automated tools to assess the security of an AWS account, identify misconfigurations, and audit against the Center for Internet Security AWS Foundation Benchmark. I was impressed with Toni de la Fuente's Prowler tool when I presented alongside him at a recent Meetup, so I added it to the training course: As it’s a cloud security course, I wanted to lead by example and include a good set of security features – which I’ll demonstrate during the course as we go through different security topics:
So I can feel that I “practice what I preach” – it wouldn’t be good for the learning platform used in a cloud security course to be missing some basic controls!
That pretty much covers the proof of concept, design, build and test of the cloud security training platform, but there’s one very important question left unanswered – how much does it all cost? I’ll answer that in my next blog post.
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
AuthorPaul Schwarzenberger is a Cloud Security Architect and DevSecOps specialist Archives
July 2024
Categories |
|
Celidor Limited
Company Number: 08870661 |


 RSS Feed
RSS Feed