|
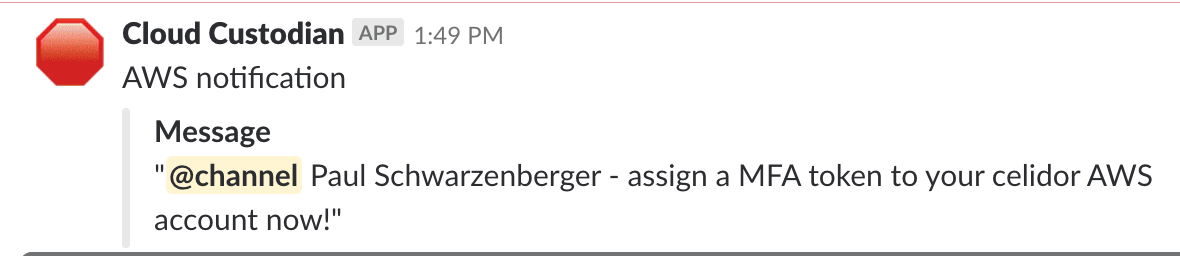
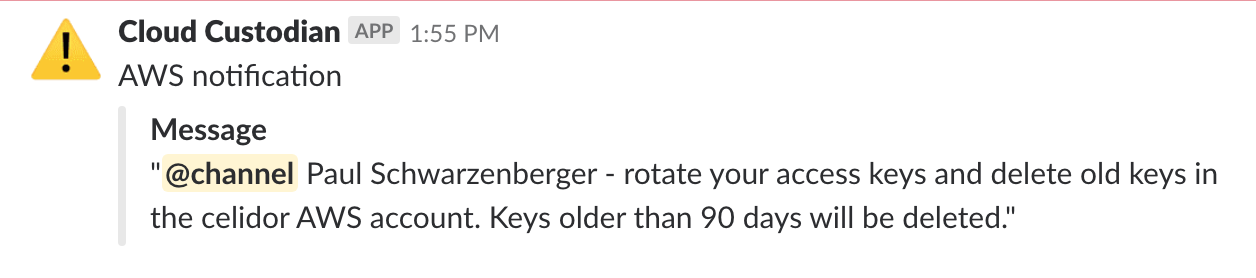
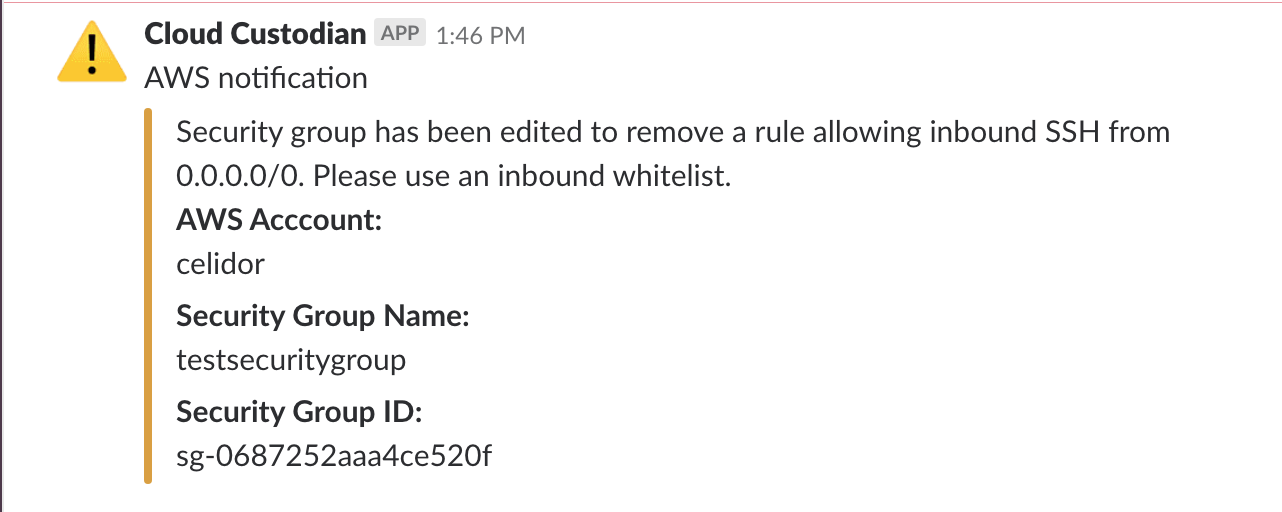
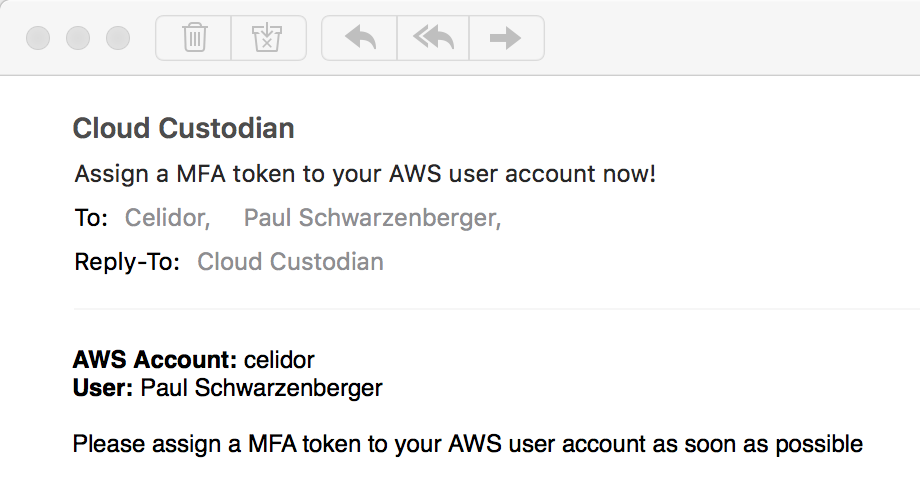
Continuous cloud compliance is essential to maintain the security of applications and systems in the cloud. At DevSecCon London next week I'll be talking about my experiences in this area, and how an effective solution needs to include prevention, detection and remediation elements. In my talk "A journey to continuous cloud compliance", I'll give a live demonstration of techniques and approaches with a system I've built in AWS using Capital One's open source Cloud Custodian project, combined with Lambda functions and other AWS services to provide customised notifications via email and Slack. Click on the read more link to see other examples of alerts and automated remediation. To comply with the CIS AWS Foundation Benchmark, access keys need to be rotated every 90 days. DevOps engineers generally need reminding of this - and if they don't comply, their keys will be deleted. Security groups - effectively host based firewalls - should never allow administrative access from anywhere, as this will open up your servers to attack: Notifications are sent via email as well as to the DevOps Slack channel:
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
AuthorPaul Schwarzenberger is a Cloud Security Architect and DevSecOps specialist Archives
July 2024
Categories |
|
Celidor Limited
Company Number: 08870661 |

 RSS Feed
RSS Feed